Category: Blog
Business Leaders are Prioritizing Cyber Risk Management – Part 2
First, in this Part 2 of Business Leaders are Prioritizing Cyber Risk Management, let’s make sure we’re aligned in terms of the definitions of Information Security and Information Risk Management, which seem to get combined or tangled in many discussions. Information security is the classic definition: “confidentiality, integrity, and availability, testing information and the systems that process or transmit information from unauthorized disclosure, unauthorized modification, and denial of service.” This is all about the security controls and assessment tools and frameworks that have been developed to protect organizations against cyber-attacks and theft. We’ll dig into these control frameworks in the next section.
Second, information risk management, on the other hand, is a different proposition altogether. Risk management assesses threats, current vulnerabilities, and the potential impact to the business objectives and mission. Risk management further assesses the likelihood of a breach and the financial or business impact of the breach. Assessing the impact in financial terms is clearly a step beyond just assessing the potential damage to the goals and objectives of the business. And to be clear, risk assessments are a part of a larger risk management strategy, where organizations assess the risks and then respond to those risks in the most appropriate manner.
In our last blog post, Business Leaders are Prioritizing Cyber Risk Management – Part 1, we quoted a recent Forrester Survey which polled IT Security leaders on their ability to quantitatively understand their organization’s level of risk. It turned out that according to the Forrester survey that we leveraged in the last blog post, less than 50% of the same were able to measure risk in with any real business metrics or dollar amounts.
Risk management assesses threats, current vulnerabilities the potential impact to the business and the cost effectiveness of IT security investments including time and technology
A critical point that companies have learned over the past several years is that they do not have unlimited resources to completely safeguard their sensitive information and the organization. When companies assess risk, as part of the risk management process, they will find vulnerabilities; they must respond to those risks or vulnerabilities by either accepting, rejecting, or mitigating, applying more controls, transferring, or sharing – these are all reasonable risk response measures.
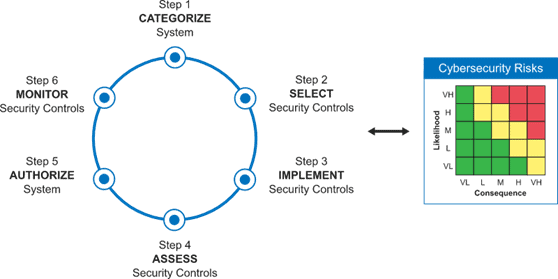
The takeaway is that there is a point of diminishing returns to IT security investments and eliminating all potential vulnerabilities does not make sense from a business perspective. All risks and vulnerabilities are not the same in terms of severity, time-sensitivity, and impact. Risk management is the processes of assessing risks and making cost-effective strategic and tactical defensive efforts to eliminate or mitigate the risk. We’ll tackle the term “cost-effective” when we pick up the BISO or Business Information Security Officer that was introduced by Forrester in a later section.
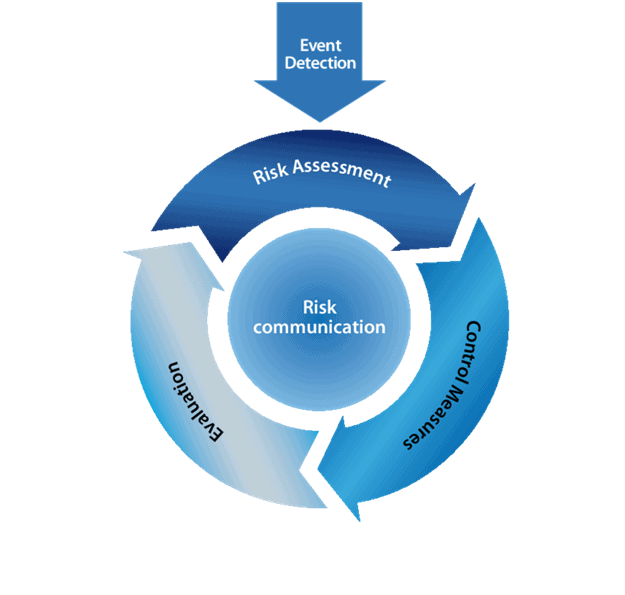
Risk Assessments are the Starting Point and a Critical Element of Risk Management
Risk assessments are an important part of any cybersecurity risk management plan. Risk assessments will outline a process for organizations to:
- Identify all of your company’s digital assets, including all stored data and intellectual property
- Identify all potential cyber threats, both external (hacking, attacks, ransomware, etc.) and internal (accidental file deletion, insider theft, malicious current or former employees, etc.)
- Identify the financial and business impact of your assets if they were to be stolen or damaged
- Rank the likelihood of each potential risk occurring
As we suggested earlier, the point of earning a positive ROI on your IT security program when all potential damage is taken into consideration is you do not have an infinite number of staff or an unlimited budget. You simply can’t protect against all attacks and eliminate all vulnerabilities – it is financially unfeasible. Thus, prioritizing risks in terms of probability and the level of impact is critical to planning and prioritizing an organizations security strategy and investments cost-effectively.
While we won’t get into the different cybersecurity control frameworks here because we will assess them in later blog posts, it is important to implement the appropriate cybersecurity framework for your company. The framework is typically dictated to some degree by the standards in an organization’s industry and region, the most frequently adopted cybersecurity frameworks are:
- Cybersecurity Maturity Model (CMMI)
- PCI DSS
- ISO 27001/27002
- CIS Critical Security Controls
- NIST Framework for Improving Critical Infrastructure Security
And most importantly their objectives and goals for organizations are as follows:
Cybersecurity Maturity Models:
- Attempt to collect the best cybersecurity practices
- Are developed by a collaboration of experts from diverse backgrounds
- Consider the dispersion in size, knowledge, skills, abilities, and experience of
- organizations that will use the model
- Take a life cycle and continuous improvement approach to cybersecurity
Cybersecurity Models help organizations
- Provide services for their customers without interruption
- Protect sensitive customer and proprietary information
- Comply with laws and regulations that govern
- their operations
Cloud vs Private Networks – How to Manage Risk Differently
We didn’t want to confuse the risk management discussion, but we did feel the need to touch on how risk management will differ in cloud environments vs private networks. A public cloud, an organization’s private network, a data center, or a mix of these will have different requirements and risk factors.
Security risk management in a public cloud involves organizations securing their own data with software, while the cloud provider secures the underlying infrastructure. Risk factors in the cloud include insecure fellow cloud customers, the cloud provider failing to secure the infrastructure, and internal employees who accidentally or intentionally spread sensitive data.
A private network requires endpoint security, firewalls, encryption of data in transit, and traffic segmentation to mitigate security risks. Risk factors for a private network include attackers gaining access to end-user devices for a foothold into the network by primarily using phishing tactics or simply luring users to malicious websites. The attackers network traffic may appear to be normal network traffic in this scenario, instead of abnormal traffic.
To manage risk in a private network, organizations can have resilient perimeter defenses as well as security programs to inspect north-south and east-west or lateral traffic moving from system to system. Data center risk factors include denial of service attacks that attack data centers with massive north-south traffic that overwhelms the website infrastructure and makes the site and data unavailable.
“The BISO” or Business Information Security Officer with Risk Management
First, let’s define how we figure out what the organization’s risk is from a mathematical perspective; this will ultimately be the top responsibility of the BISO – it is Risk = Threat x Vulnerability x Consequence. While it’s not critical to use actual numbers for each of the components of the equation, the closer an organization can get with numbers the better it will be able to manage its overall risk.
Risk = Threat x Vulnerability x Consequence or Damage
Second, IT led by the CIO and InfoSec led by the CISO have vastly different priorities and goals; with that, gaps are created for attackers to exploit. IT professionals are focused on the functional execution of an organization’s business; on enabling the organization to achieve its goals by leveraging technology to achieve operational success. That means finding and deploying technology tools and platforms that enhance communication, facilitate information sharing, and support more efficient business processes. CIO’s and their IT team prioritize technology’s functionality, availability, performance, and accessibility, at a cost that achieves a desired return on investment.
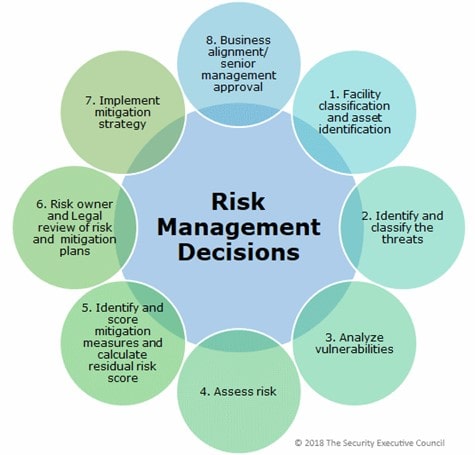
InfoSec’s basic priorities, on the other hand, are to eliminate all information security risks to the business – to keep it simple. They evaluate technologies being adopted by an organization, the business processes they support, and the staff responsible for those processes, and then create defense strategies against those risks.
There is a conflict between managing enterprise IT systems that increase productivity and profits (CIO) and protecting the organization from cyber-threats (CISO)
Enter the BISO and the evolution of risk management. The BISO bridges the disconnect between the CISO and CIO. The Forrester report that we leveraged in Part 1 of this blog post series polled nearly 850 security and business executive who suggested “85 percent of BISO-type security leaders say they have metrics for tracking the return on investment and business performance impact of cybersecurity projects.”
Thus, BISO’s are the natural evolution of CISO’s. CISO’s were forced into the role of playing “whack-a-mole” with security vulnerabilities purchasing Firewalls, IDS/IPS, Anti-virus, Endpoint Protection, and other defense technology to stop the increasing number and diversity of attacks. Meanwhile their budgets exploded, and attackers slipped through the layered defense strategies anyway.
BISO’s are tasked with finding the right balance concerning security investment and business need. Their goal is to protect the business cost effectively and stop security investments when they evaluate that they have entered the land of diminishing returns on security investments. BISO’s need to understand what is required to protect the businesses most critical security needs as well as its evolving privacy and compliance needs.
Risk Management is the Key to a Successful IT Security Program
As we said in our “Part 1” of this blog post – in the Forrester survey, 94% of security and business executives found that their organization have experienced a “business-impacting” cyberattack or compromise in the past year. Thus, executives now have a critical mass or large enough sample to estimate the cost of an attack. Further, they are beginning to understand the potential liabilities from compliance and privacy violations that likely fall under the umbrella of IT security responsibilities.
With that, BISO’s or CISO’s have the responsibility to protect the business cost-effectively and have the ability to make security decisions from a profit and loss perspective. They are tasked in many cases with preventing the CISO’s or heads of IT Security from spending on defense technology beyond the point of diminishing returns and evaluating the investments so that they make sense for the business they represent.
We have no doubt that most of the folks reading this post that will be in businesses will not require the role of a BISO. However, risk management in the vast majority of companies needs to evolve to incorporate costs and benefits from an IT Security standpoint. Risk management is about quantitatively evaluating the business risks and making strategic IT security investments to minimize the risks to a level that makes sense for the business.
Conclusion
Although it’s slowly becoming more common for IT to have “a seat at the table” in boardroom meetings, as we said, many companies still separate business and IT into distinct divisions. The way IT interconnects with almost every business operation naturally results in an increased risk profile. The evolving dependence of the business on IT means IT events – data loss, corruption, security breaches and infrastructure failures – can no longer be confined to the department in which they occurred. When one of these IT events occurs now, the whole organization’s productivity, reputation, and ability to achieve strategic goals are hampered.
IT security risk will always exist; however, by improving alignment this can be continually monitored and communicated meaningfully to stakeholders. A proactive risk approach will enable the business to operate more cost-effectively, become more agile and respond to change with more informed, measured decisions.


