Category: Blog
The Outlook for Data Privacy and Security in Jamaica?
Ah, Jamaica. The mention of this Caribbean Isle conjures up pleasant thoughts of swaying palms, beautiful beaches, reggae music, and good Jamaican rum. However, like most rapidly digitizing nations, Jamaica isn’t immune to the scourge of cybercrime.
In this post, we’ll turn the spotlight on the issue of cybersecurity and data privacy in Jamaica, considering the nature and scope of the current threat and the steps the government and businesses are taking to better protect themselves.
Jamaica Has Been Experience Increasing Cyber Crime
With a population of 2.98 million, Jamaica is the third-most populous Anglophone nation in the Americas, after the U.S. and Canada. In January 2022, there were 2.03 million internet users in Jamaica. This represents about 68.2% of the total population, a figure that’s up from around 55% in 2017. Cybersecurity attacks have been increasing in Jamaica and the rest of the Caribbean and Latin America at a rate commensurate with the region’s ongoing digitization:
- In early 2021, the Jamaican government fell victim to three significant security breaches relating to its JamCOVID app – a platform designed to connect citizens and travelers with resources to help them manage their travel, quarantine, symptom checking, and other COVID-related matters.
- In the first six months of 2022, the Caribbean experienced 144 million cyberattack attempts, with ransomware being the most common breach.
- Guyana was the most popular target with 71 million attempted cyberattacks, Suriname experienced 16 million, Barbados was third with 13 million attempts, and Jamaica fourth with 12 million.
- Businesses in Latin America and the Caribbean paid out approximately $124 million in the first half of 2022 for ransomware attacks.
In October 2022, a cyberattack on Massy Distribution Jamaica, one of the country’s largest suppliers of consumer and pharmaceutical goods, made headlines. This was the second cyber-incident to hit a member of the Trinidad-based Massy Group this year. In April, a ransomware attack forced the company to close stores in Trinidad and Tobago. Hackers effectively froze the grocery chain’s point-card system and exfiltrated approximately 216 gigabytes of data before encrypting it. It’s alleged that the exfiltrated files were subsequently posted on the dark web. The country’s financial institutions are frequent targets to these attacks.
The 2018 Financial Stability Report published by The Bank of Jamaica (BOJ) revealed that banks in Jamaica were falling victim to an average of about two cyberattacks every week and that threat actors had siphoned up to $10 million in a single month. At that time, average losses stood at over $4 million per month.
The 2021 report, published in March of this year, noted that between January 2018 and October 2021, bank fraud losses averaged $1 billion per annum. This figure represents about 0.05% of Jamaica’s gross domestic product. It also noted that debit and credit card fraud was the most prevalent, accounting for 84.6% ($3.3 billion) of fraud losses over the period. Incidents of fraudulent wire transfers, cheques, and loans; internal fraud; and Internet banking fraud were also widespread.
The BOJ also highlighted a concerning spike in SIM swap scams, whereby fraudsters attempt to access online banking platforms via mobile numbers tied to customers’ accounts. Consumers who are defrauded in such cyber-incidents often face a long and uphill battle to get their money returned, as one victim explained in a recent news article:
“I must tell you that in Jamaica, recovering stolen money can be an extremely long and frustrating process. I was the recent victim of an attack. All of my money was wiped out of my accounts, and cash advances taken from my credit cards. This happened the day that my salary went into the account.
“When I contacted customer care, they sent me to the closest branch to make a formal report. I was at the branch from 8:15 a.m. to 3:50 p.m. At the end of the day, I was told that recovering my month’s salary along with the other funds taken from my account would take between 30-120 days.”
Bolster Security & Privacy Defenses in Jamaica
In response to the concerning increase and sophistication of cyberattacks in the country, the Jamaica Cyber Incident Response Team (JaCIRT), which monitors and responds to cyber threats, has embarked on public awareness initiatives to educate targeted groups about how they can better protect themselves. JaCIRT has engaged directly with over 80 entities over the course of the last financial year as part of this effort.
In addition, with the assistance of the Organization of American States, it’s deployed an early warning system that allows it to see attacks happening in real-time, monitor attackers’ activities, and respond accordingly. According to Jamaica’s Minister of Science, Energy, and Technology, Daryl Vaz, “This facility provides invaluable insight into attacks, which are used to provide assistance in reducing the likelihood of recurrence and shortening response time.”
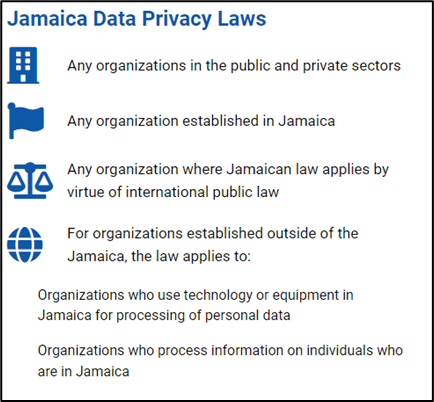
Jamaica, along with other jurisdictions in the region, has also advanced along the anti-cybercrime legislative path by passing data privacy legislation similar to the European General Data Privacy Regulation (GDPR).
The Data Protection Act of 2020, enacted in May 2020, applies to any individual or entity that collects the personal data of any individual. The Jamaican Data Protection Act 2020 (“JDPA”) is Jamaica’s first comprehensive privacy law, governing the collection, process, storage, use and disclosure of personal information. CONSENT is the legal basis for processing information, and shall be determined “freely given” by either a written statement or an affirmative act that signifies the agreement of processing personal information.
According to the Act, such parties must design organizational and technical controls that safeguard how they use sensitive personal data or risk facing severe non-compliance fines or even imprisonment. Here are some of the Act’s key requirements and specifications:
- The Act defines a “data controller” as any person or public authority that determines the purpose and manner for processing personal data collected from individuals.
- It applies to any data controllers that are established in Jamaica or any entity that processes personal data through Jamaica, regardless of its physical location.
- Any entity that processes the data of an individual who is in Jamaica while offering a product or service to individuals in Jamaica, or any entity that monitors the behavior of subjects within Jamaica, also qualifies as a data controller.
- Every individual or entity that qualifies as a data controller in terms of the Act must appoint a data controller representative. This person must be a Jamaican resident, an entity established and formed in Jamaica or someone who maintains a regular practice in Jamaica.
- The data controller is legally required to report any data breach within 72 hours of becoming aware of it.
While these initiatives and regulations may be seen as welcome progress in the battle to curb cybercrime in Jamaica, businesses need to ensure they’re also stepping up to protect their employees, customers, and shareholders from the devastating impact of a successful data breach. Let’s explore some ways to do this:
Steps to Building Your Cyber-resilience
- Strictly enforce software updates: Yes, many employees find these annoying, but the benefit-to-cost ratio is significant. That’s because many software updates include patches for known security gaps, so without them, you’re leaving systems vulnerable to avoidable breaches.
- Tighten up your password protocols: Sometimes, people just make it too easy for hackers to breach their networks. If your users and administrators routinely use (and reuse!) standard, insecure passwords, you’re at risk. Make sure everyone knows that their passwords must be complex, incorporating different characters, cases, and numbers. They should also be changed regularly and never duplicated across applications or websites. Also, add two-factor password authentication.
- Use inbound email scanning: These tools protect you against malicious actors sending harmful attachments or pretending to be a company’s executive or another influential figure.
- Perform routine data backups: If you already have your data stored on a separate system, you’ll avoid being held hostage by a ransomware attacker, even if they do compromise your systems.
- Engage with a managed security service provider: Building and maintaining a strong cybersecurity posture can be a complex and costly endeavor if you try to go it alone. Managed security service providers are in the business of delivering reliable cybersecurity, compliance, and data privacy solutions for organizations of any size and in any industry.
Conclusion
There are encouraging signs that Jamaica’s government and business community are joining forces to combat the ongoing cybersecurity threat to the Jamaican economy and its citizens’ livelihoods.
We think the Head of JaCIRT, Lieutenant Colonel Godphey Sterling summed it up best in a recent address:
“Businesses must also recognize the important role they play in the whole cybersecurity ecosystem [and understand] that resilience can only be achieved if we all play our part. As far as the cost for being cyber secure [is concerned], not being cyber secure will cost much more. Let us move forward with our different strengths and weaknesses and, in a collaborative way, build on these so that we can help to build the capability of the cybersecurity ecosystem in Jamaica.”
They Hitachi Systems Security team recommends a Privacy Impact Assessment (PIA) which is a structure review of an information system to identify and mitigate risks, including risks to confidentiality, at every stage of the system life cycle. PIA states what personally identifiable information (PII) is collected and provides a systematic means of answering questions such as:
- What personal data are you processing?
- How is it being processed?
- What are the existing measures for data protection??
- What aspects of processing can potentially cause harm to concerned individuals, the organization, or the public?
- How can the risks of harm be addressed?
Ultimately your organization will have clarity concerning the gaps that are in the environments which could be potentially exploited by bad actors. For more information, reach out to our Team in the region – Contact Us.


