Category: Blog
Fundamentally, cyber risk management means identifying, analyzing, evaluating, and addressing your organization’s cyber security threats including their potential impact on your business. The first part of the cyber security risk management process is a cyber risk assessment. This risk assessment will provide a snapshot of the threats that might compromise your organization’s cyber security and how severe they are.
Based on your organization’s risk appetite, your cyber risk management program then determines how to prioritize and respond to those risks. Let’s look at where most organizations are in terms of implementing risk management risk strategies by leveraging an excellent report by Forrester. According to study, less than 50% of IT Security leaders are able to measure or quantitatively understand their organization’s level of risk. In addition, just 51% of the security pro’s that were surveyed were able to identify their organization’s level of risk from a business perspective.
It is important to understand what is meant by risk management, measuring risk, and reducing risk. A significant number of organizations and security leaders see risk management as theoretical rather than something measurable that their organization should strive to identify and set goals to reduce. Most professionals in the IT security or cybersecurity industry understand it is difficult to set a dollar value to systems, data loss costs, litigation costs, brand damage costs, ransomware costs, compliance penalties and so many other difficult to estimate variables. However, just as equity analysts try and predict the expected outcome of an investment with sensitivity and scenario analysis using among a variety of variables, cyber leaders should partner with the business side of the organization to try estimate the value of company assets and the risk to those assets.
In another excellent survey, Travelers who offers cybersecurity insurance coverage for cyber-attack losses conducted a survey that asked business leaders about their security best practices. Several of the questions asked in the survey that drew our attention included the following year over year comparison data:
- Updated their computer passwords (74%, up from 71%).
- Purchased a cyber insurance policy (51% of survey participants, up from 39% last year).
- Created a business continuity or disaster recovery plan in the event of a cyber-attack (47%, up from 38%).
- Executed a risk assessment across their IT infrastructure (49%, up from 45%) and their vendors (41%, up from 37%).
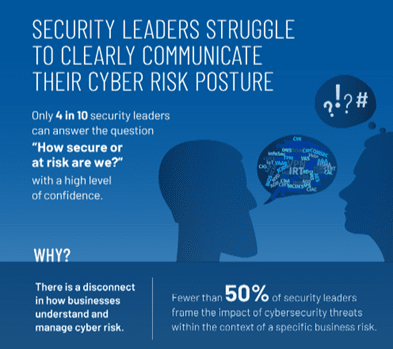
In a third study by Forrester and Tenable, they found that just four out of ten security leaders can answer with a high level of confidence the question: “How secure, or at risk, are we?”
Heather Vallis, a principal consultant at Forrester who led the project, says only 66% of business leaders say they were, at best only somewhat confident in their security teams’ ability to answer that question.
“The core issue is that business and cybersecurity strategies are seldom on the same page,” Vallis says. “Strategies are created in a vacuum, security leaders have an incomplete view into enterprise assets, benchmarking is limited, and cybersecurity metrics often lack business-risk context.”
Aligning InfoSec and Business Goals has Become Critical
In security operations, we understand that security responsibilities, in and of themselves are time consuming and difficult. For example, the constant system patching, conducting vulnerability assessments, executing penetration tests, tuning SIEMs and Firewalls and going through almost endless system logs does not leave too much time to meet with other organizational leaders to calculate risk.
Forrester suggested fewer than 50% of security leaders frame the impact of cybersecurity threats within the context of a specific business risk. Further, just over half (51%) say their security organizations work with business stakeholders to align cost, performance, and risk reduction objectives with business needs. And just four out of 10 (43%) say they regularly review the security organization’s performance metrics with business stakeholders.
Vallis says security respondents answered a series of questions assessing their practices across oversight, technology, process, and people. Respondents scoring in the top 25% were categorized as “business-aligned,” while those falling in the bottom 25% were “reactive and siloed.” She says security leaders who take a proactive approach to risk that’s aligned to the business are eight times as likely as their more reactive and siloed peers to be highly confident in their ability to quantify their organization’s level of risk or security (72% vs. just 9%, respectively).
We found the Forrester findings to be aligned with what we see across businesses and from industry to industry. What we mean is that if an organization has put themselves through a security posture assessment like CIS, ISO, or NIST, that exercise will force them to evaluate high-value systems, their security hygiene processes, and their path to more effective security defense…at a minimum.
What seems to be evident in their survey is that the majority of organizations still have not put themselves through a valid assessment.
Forrester Introduces “The BISO” or Business Information Security Officer
Vallis says more companies need to consider putting in place a business information security officer (BISO). Business-aligned security leaders are more than twice as likely to have a BISO or someone with similar responsibilities who ensures each line of business works to minimize risk, maximize protection, and increase the value of the organization’s business information assets.
“These executives collaborate with line-of-business leaders to develop strategies, goals, and metrics to maximize the protection of business information assets,” Vallis says. “They help bridge the ‘language barrier’ between security and business,” she adds.
Ultimately a BISO should fully incorporate the risk-based cybersecurity program into the enterprise risk management framework, which functions as the organizing principle for analyzing and classifying enterprise risks. The framework should not be used as a general guideline, but rather as the organizing principle. By framing cyber risk as a business risk, this approach makes cyber risk management more intelligible to businesses.
Risk = Threat x Vulnerability x Consequence or Damage
Risk management is critical to Hitachi Cyber and the organizations that we serve so we wanted to understand more about the role and responsibilities of the BISO. First, let us take a step back and define the roles and responsibilities of the CISO. The CISO is an executive position tasked with executing the information security and risk management goals as defined by senior officers. CISOs develop and oversee the enterprise’s cybersecurity strategy, including cybersecurity policies and controls.
So CISO’s have traditionally had the responsibility of risk management and based on what we have seen in the evolving threat-ridden IT security environment, these folks are overwhelmed. CISO’s have seen threats to their organizations rise exponentially over the past several years, the technology in their organizations change dramatically, and now with Covid-19, their workplaces and how employees connect to systems change significantly. Frankly, from our perspective, CISO’s neither had the time or the mandate to measure risk in all but the largest and most sophisticated organizations.
6 Steps to Implementing a Risk Management Program
In the Forrester survey, 94% of security and business executives found that their organization have experienced a “business-impacting” cyberattack or compromise in the past year. Business-impacting according to the survey is defined as an attack that resulted in the loss of customers, employees, or confidential data (PII). Further, any interruption of day-to-day operations, a ransomware payout, or other financial loss or theft of intellectual property would be included.
“That’s a very powerful number, especially when talking to the executives in the C-suite,” says Wenzler. “Security pros can now go to top management and offer proof that cyberattacks will impact their businesses and that they have to do something about it.”
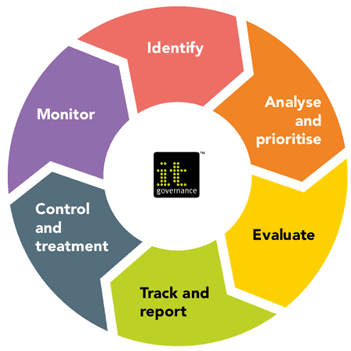
A Risk Management Program typically follows these steps:
- Identify the risks that might compromise your systems and organization. This involves identifying cyber security vulnerabilities in your system and the threats that might exploit them.
- Analyze the severity of each risk by assessing how likely it is to occur and how significant the impact might be if it does.
- Evaluate how each risk fits within your risk appetite, or plainly speaking, what can you afford to lose with the understanding that you don’t have an unlimited budget to protect your organization against all risks.
- Prioritize the risks using the value of the system, threats to the system and vulnerability criticality or score.
- Decide how to respond to each risk. There are generally four options:
- Treat – modify the risk’s likelihood and/or impact typically by implementing security controls.
- Tolerate – make an active decision to retain the risk – you can’t patch everything the moment the patch is released so create rolling timelines to test and install the patch for example.
- Terminate – avoid the risk entirely by ending or completely changing the activity causing the risk.
- Transfer – share the risk with another party, usually by outsourcing or taking out insurance.
Risk management is a continual and hopefully improving process. As your organizations moves up the security maturity curve, they should monitor continually update risks and vulnerabilities, Review your controls to ensure they are still fit for your purpose, and make changes as required. Remember that your risks continually change as the cyber threat landscape evolves, and your systems and activities change.
Conclusion
In part 2 we’ll discuss the importance of risk assessments as well as the challenges that organizations must overcome in order to implement a cost-effective risk management program. We’ll take a deeper dive into creating a risk management program that aligns the goals of the IT security team or the goals of the business and measures the effectiveness of security investments and the potential monetary damage from various cyber-attacks that the organization is likely to face in the future.
Forensic examiners and threat intelligence professionals tell us cyberattacks are typically not random. There are usually signs of a planned attack against an organization. Typical signs of an imminent attack include mentions of the organization on the dark web, the registration of similar domain names to be used for phishing attacks, and confidential information, such as user account credentials, put up for sale.
As we conclude with part 1, we want to provide a definition that most business leaders are using for cybersecurity risk management: “Cybersecurity risk management takes the idea of real-world risk management and applies it to the cyber world. It involves identifying your risks and vulnerabilities and applying administrative actions and comprehensive solutions to make sure your organization is adequately protected.”
This definition has evolved, as we stated earlier, to add calculating the expected monetary damage from attacks, ROI of security investments, and critically, the diminishing marginal returns from each incremental security investment. The International Organization for Standardization (ISO) defines risk as “the effect of uncertainty on objectives.” A cyber risk management process is about managing the effects of uncertainty in a way that is cost-effective and makes efficient use of limited resources. Risk management helps identify risks early and implement appropriate mitigations to prevent incidents or limit their damage. That definition from ISO will lead us into part 2 where will discuss the risk management process and risk management assessments.


