Category: Blog
The Wisdom of Taking a Human-Centric Approach to Cybersecurity Awareness Training
Traditional approaches to security awareness training are missing the mark miserably. If you assume your employees have a solid grasp of cybersecurity best practices, this news may be unsettling.
The problem is that cybersecurity awareness training remains largely a “tick-box” exercise in most organizations. It relies heavily on simulated attacks designed to expose how susceptible employees are to attacks, particularly phishing attacks. Often, this does little more than embarrass people, making them see security teams as antagonists rather than allies.
Worse still, such initiatives rarely result in positive changes to user behavior, which makes them poor investments. In this article, we’ll explore the flaws of traditional cybersecurity awareness training initiatives and consider how security leaders can redesign their programs with the human mind as the focus.
The Anatomy of Cyberattacks Targeting Employees
Most attacks targeting employees involve some form of opportunistic phishing in which cybercriminals send their targets fraudulent communications that appear to come from a reputable source.
The goal of these schemes is to steal money, either by obtaining it directly from the organization or by using employees’ personal information to commit identity theft. Unfortunately, there’s a low risk and high return for cybercriminals engaging in these behaviors.
The Most Common Types of Phishing Attacks Include:
Email Phishing
This is the most common type of phishing, and it’s been around since the 1990s. Hackers aren’t particularly selective about who they send such emails to – they’ll distribute them to just about any email address they can obtain. Phishing emails typically inform the target that there’s been a compromise to one of their bank accounts or that they’re the recipient of an unexpected financial windfall.
Either way, users are told they need to respond immediately by clicking on a supplied link to verify their bank account number, SSN, etc. Once the attacker receives the information, they can take control of the user’s bank account.
Smishing
Smishing attacks are phishing attacks distributed via SMS. Smishing is a form of phishing in which an attacker uses a compelling text message to trick targeted recipients into clicking a link and sending the attacker private information or downloading malicious programs to a smartphone. Users are much more trusting of text messages, so smishing is often lucrative to attackers phishing for credentials, banking information and private data.
Spear Phishing
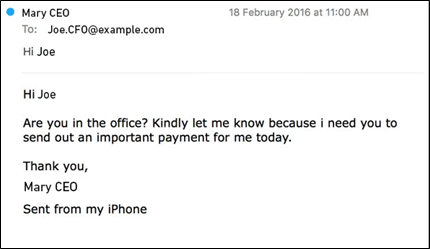
Spear phishing attacks target a specific type of individual in an organization. They involve well-crafted messages that appear to come from what looks like a trusted source, authorized entity, or the employee’s superior or other senior-level managers. Below is an example of what a spear phishing email could look like – this email appears to come from a CEO asking her CFO to make an urgent payment:
Vishing
These are voice phishing telephone calls. Often, vishing attacks involve a call from someone claiming to be a representative from organizations like Microsoft for example, who informs the target that they’ve detected a virus on their computer. The target is then asked to provide credit card details so the “representative” can install updated anti-virus software on their computer.
In addition to gaining their victim’s credit card information, the attacker will likely install malware on their device. This malware frequently comes in the form of a banking Trojan that watches the target’s online activity to steal more personal details, such as their banking passwords.
Whaling
Whaling is an even more targeted type of phishing scam that targets a CEO, CFO, CHRO, or other senior-ranking employees within a company. A whaling email might inform the recipient that the organization is facing legal action and that they need to click on the link for more information on the case. These links usually take targets to a web page where they’re asked to enter critical data about the company, such as their tax identity and bank account numbers.
To give you an idea of how devastating this type of attack can be, here are a few recent examples of executives that fell victim to whaling scams:
In 2016, the CEO of the Austrian aerospace company FACC was fired for his role in a whaling attack that cost the organization around $58 million. In a statement, the company stated that the CEO, Walter Stephen, had “severely violated his duties” by allowing the attack to take place.
In 2020, the co-founder of a prominent Australian hedge fund, Levitas Capital, followed a fake Zoom link that installed malware on the company’s network. The criminals tried to use fraudulent invoices to steal $8.7 million but only managed to siphon off $800,000 before being detected. However, the fallout from the incident cost Levitas its biggest client, ultimately forcing the hedge fund to close.
Traditional Security Awareness Training isn’t the Answer
Security awareness training has been lauded as the answer to reducing organizations’ susceptibility to cyberattacks targeting their employees.
According to Proofpoint’s 2022 State of the Phish Report, a whopping 83% of organizations said they had suffered successful phishing attacks last year. Of them, 54% ended in a customer or client data breach.
However, these interventions aren’t delivering the expected outcomes, and people continue to be the most targeted vulnerability in businesses’ security chains. The following statistics attest to the flawed nature of traditional cyber-awareness training:
- In 2021, low security awareness among employees was the top barrier for organizations looking to establish effective defenses.
- Employees’ understanding of phishing dropped 15% during 2021.
- Over the last year, eight in 10 data breaches involved people-related vulnerabilities, such as employees falling for phishing attacks and other social engineering tactics.
- 70% of users whose credentials have been exposed in breaches are still using the same passwords.
- Email-based compromises increased by 35% in 2021, costing U.S. businesses over $2.4 billion.
The fact that nearly 80% of organizations report that email usage is on the rise (and that researchers reported an increase in email-based threats over the past year, 26% of which they labeled as “significant” threats doesn’t bode well for the future of corporate information security.
Traditional Social Engineering and Security Awareness Training has not Been Effective
So, where are we going wrong? As we touched on earlier, part of the problem is that employee security awareness training depends overly on periodic mock phishing email tests. Security teams track user failures and use the results as indicators of overall employee-related security vulnerability.
But this can be counterproductive, as employees often start feeling resentful, victimized, or feel that they are being monitored by “big brother.” These feelings can manifest in what’s termed “fear fatigue,” which is defined as “demotivation to follow recommended protective behaviors, emerging gradually over time and affected by a number of emotions, experiences, and perceptions.” This sentiment was reported by 80% of respondents in a recent survey. Equally concerning, fear fatigue can often lead to careless employee behavior.
In addition, little scientific data exists to support this method of training. Consider the findings of one study into this area:
“To explore the effectiveness of embedded training, researchers conducted a large-scale experiment that tracked workers’ reactions to a series of carefully crafted spear phishing emails and a variety of immediate training and awareness activities. Based on behavioral science findings, the experiment included four different training conditions, each of which used a different type of message framing.
The results from three trials showed that framing had no significant effect on the likelihood that a participant would click a subsequent spear phishing email and that many participants either clicked all links or none, regardless of whether they received training. The study was unable to determine whether the embedded training materials created framing changes in susceptibility to spear phishing attacks because employees failed to read the training materials.”
The Role of Cognitive Bias in Successful Phishing Attacks
In the 1970s, cognitive psychologists discovered that, in certain circumstances, people show a systematic deviation from norm or rationality in judgment – a phenomenon termed cognitive bias. These deviations to our regular thought processes are our brains’ way of expediting and simplifying information processing. As such, they can also affect decision-making relating to workplace cybersecurity.
Unfortunately, cybercriminals are all too aware of this element of the human psyche – and exploit it to the maximum. Most scams are designed to create a sense of panic or fear. For example, by posing as an authority figure (an irate manager or impatient CEO) or a threatening or intimidating authority body (a business ethics commission or the IRS), they often successfully trigger powerful, knee-jerk emotional reactions. SecurityAdvisor recently assessed more than 500,000 malicious emails to explore the cognitive biases exploited by attackers to target employees. They found that authority bias, where a cybercriminal pretends to be a person of authority in the user’s organization, was among the top five cognitive biases exploited in spam and phishing schemes.
Creating Successful Security Awareness Training is Critical
By improving security teams’ and employees’ understanding of cognitive biases, it becomes easier to identify and mitigate the effects of flawed reasoning. For example, to combat authority bias, organizations can design more meaningful security awareness training that coaches people to take a moment to think carefully about “urgent” requests – wherever they appear to come from – and not rush to fulfill them.
With such an approach, it’s easier and more effective for security teams and employees themselves to identify and mitigate the impact of psychologically powered phishing scams.
Conclusion – Security Awareness Training Does Work After All
Ultimately, technical knowledge isn’t fail-proof, and all the training in the world won’t help when attacks exploit people’s greatest fears and vulnerabilities.
Security teams need to reimagine their approach to employee security awareness for the simple reason that training humans isn’t like defining a rule base in a firewall. It’s easy to program a firewall to allow certain forms of network traffic and block others based on the attributes of the traffic. Firewalls will reliably and predictably follow the rules you’ve set. People, however, won’t necessarily always follow the guidance they’ve received on how to identify, resist, and report on various types of cyberattack. That’s because, unlike machines, people don’t always follow a purely logical thought process; they’re often swayed by their emotions.
With so many different factors playing into the success of security awareness training — including company size, location, and training costs — it’s pretty difficult to produce an accurate prediction of figures that can be relevant to every business.
That said, the Osterman Research has produced one of the most renowned costs and ROI models developed for security awareness training.
Their study showed that, on average, smaller businesses (under 1,000 employees) can achieve an ROI of 69% from a security awareness training program, while larger companies (1,000+ employees) can achieve an ROI of 562%.
The caveat here is that the report has been based on a range of assumptions — which you can check out in more detail in the Osterman Research we referenced earlier. Their research takes into account a variety of variables including costs of operations and the potential loss of customers and revenue, which obviously varies from business to business.
But don’t get too lost in the data. The key point is — training does work.
In our experience, there are 5 key elements to a successful, people-centric security awareness training program:
- Set the tone from the top: Senior management needs to do more than simply approve the training budget; they must also be willing consumers of the training, rather than ordering those beneath them to go through it while not participating themselves.
- Make it fun: Seek out vendors that offer fun quizzes, micro-learning experiences, and gamification to keep employees engaged.
- Keep it fresh and relevant: To increase the interest levels in your training, content should be delivered regularly in segments that are aimed at targeted topics relevant to your organization.
- Ask employees for feedback: What do they think of the format? Does it have visual appeal?
- Measure effectiveness in a non-threatening environment: Regularly test employees’ knowledge of key concepts taught during training modules without introducing fear of failure or judgement.
Improving employee security awareness will be most impactful if it’s people-centric and works naturally with the human mind. Such initiatives are more likely to lead to fundamental changes in individuals’ behavior and, ultimately, improve the entire organization’s security posture.


